This is the final installment of a three-part blog series where CSC® explores how the WHOIS database has become a window into the security set up of an organization due to the ever-increasing threats of cyber crime. Click here to find out the #1 and #2 threats to domain security in previous posts.
#3 threat: unauthorized access
 Our focus in this post is on the security information available and what it tells would-be attackers about a company’s ability to mitigate domain name system (DNS) hijacking and domain shadowing. We’ll discuss some effective and cost-efficient protections companies can put into place to evade attacks, such as registry- and registrar-level locks, two-factor authentication, and domain name system security extensions (DNSSEC).
Our focus in this post is on the security information available and what it tells would-be attackers about a company’s ability to mitigate domain name system (DNS) hijacking and domain shadowing. We’ll discuss some effective and cost-efficient protections companies can put into place to evade attacks, such as registry- and registrar-level locks, two-factor authentication, and domain name system security extensions (DNSSEC).
Domain locks
Domain name locks were first introduced in the .COM domain extension in response to bad actors gaining legitimate access to registry and registrar platforms, and making unauthorized changes to domain name records. A registrar lock inserts a manual authorization process between the requestor and the registrar, before the registrar processes that request. A registry lock inserts a manual authorization process between the registrar and the registry. In both cases, it is possible to block three distinct requests:
- Deletions. The locks ensure a domain name cannot be deleted or lapsed without the proper authorization.
- Transfers. Both locks can reject unauthorized transfers away from the existing registrar.
- Updates. Neither lock allows WHOIS information modification, including name server re-delegations.
It is also possible to put a lock on renewal, but this is not considered good practice as it would mean that a company would have to unlock a domain before every renewal, negating the auto renewal function, which could be detrimental, especially for critical domains.
Organizations should prioritize all business critical domains to be locked. The status codes for locked domains indicated by some WHOIS such as .COM are as follows:
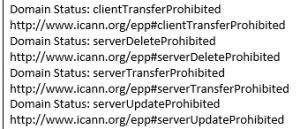 Status with registrar locks applied:
Status with registrar locks applied:
- ClientDeleteProhibited
- ClientTransferProhibited
- ClientUpdateProhibited
Status with registry locks applied:
- ServerDeleteProhibited
- ServerTransferProhibited
- ServerUpdateProhibited
All of these locks are optional except for “ClientTransferProhibited,” which the Internet Corporation for Assigned Names and Numbers deemed mandatory for all generic top-level domains (gTLDs). With the state of security today, registries of country-code TLDs are recognizing the importance of such locks and are slowly rolling out lock programs. CSC currently offers locks in all extensions that registries support.
In January of this year, CSC’s Cyber Security Report reported that little over 50% of large brand owners are utilizing locking services. And in a further analysis of nearly 15,000 organizations with .COM or .NET core domains, we found that only 6% of companies have MultiLock (both registrar and registry locks) in place.
Sadly, the message unsecure domains are sending to bad actors is that there is both weakness and opportunity for cyber crime.
Two-factor authentication
Two-factor authentication is a method of confirming a user’s claimed identity by utilizing a combination of two different components. A username and password are the first component, and a unique one-time code is usually the second.
Although it’s not possible to see from the WHOIS whether a domain is protected by two-factor authentication, it’s important to share that in CSC’s experience, there is a correlation between those companies that have not invested in MultiLock for their core domain and those that have not invested in two-factor authentication on their domain name portfolio. Although most consumers now use two-factor authentication in its various forms for our banking needs, many corporate domain name portfolios don’t have this security step in place (does your domain provider offer it?). Certainly, the value of the digital assets within any of the domain name management platforms is far greater than anything in most people’s bank accounts!
DNSSEC
Vulnerabilities in DNS Services allow attackers to hijack the process of looking up services on the internet. DNSSEC is a solution to those vulnerabilities. For example, directing traffic to a spoofed site designed to collect user names and passwords is made more difficult when DNSSEC is fully implemented.
By “digitally signing” the root zone, users can confidently navigate to a brand’s site without being redirected to a spoofed site. Although cheap to implement, CSC’s research suggests that less than 1% of core domains for organizations make use of the DNSSEC security measure.
Summary
Publicly available WHOIS information is so much more than the contact information for the owner of a domain. It is a window into a brand’s approach to security. If companies make the WHOIS work for them, WHOIS can act as a deterrent to the cyber criminals looking for their next target.
If you are interested in reviewing the level of information available on your WHOIS, contact CSC for a complimentary security audit of your digital assets.
Domain Security, Part 1: Do You Know Who’s in Your WHOIS?
Domain Security, Part 2: You’re Only as Secure as Your Provider